 From turning a Smart TV into a surveillance device to a discussion of the economics of the digital arms market, and many, many deep dives into hacks — that’s Breakpoint Day 1.
From turning a Smart TV into a surveillance device to a discussion of the economics of the digital arms market, and many, many deep dives into hacks — that’s Breakpoint Day 1.
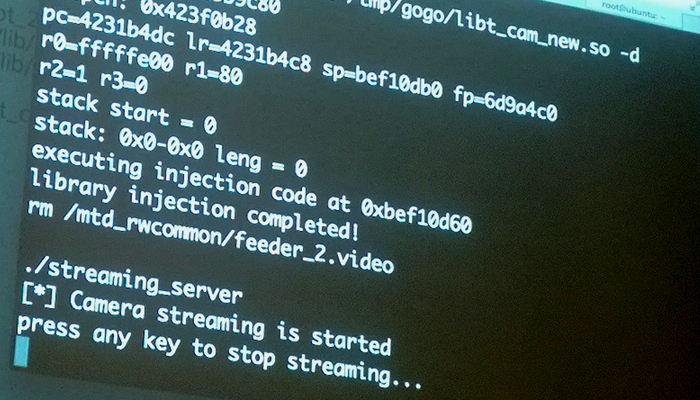
My personal highlight was a demonstration on how to hack a Smart TV from “an unnamed vendor” — a large non-Japanese company whose name stats with a consonant from the second of half the alphabet — by SeungJin Lee.
Lee’s presentation showed how appallingly insecure one model of this vendor’s Smart TVs were — all the applications ran as “root”, the administrative user, for example, which means that a malicious app could do pretty much whatever it likes — and how the camera and microphone-equipped devices could be turned into video surveillance machines.
“Do not put the Smart TV in the bedroom,” he said. Good advice.
Lee also showed how he could pop up a fake news headline graphic over the top of the genuine live video stream from a news channel. The possibilities for mischief are obvious.
Michael Sulmeyer, a senior fellow at the Center for Strategic and International Studies in Washington DC, discussed the economics of the digital arms market.
Traditional arms markets for weapons of national power and prestige are what he called a “monopsony”, with the government being the only buyer, and only a handful of vendors. Prices are high, and get higher as projects unfold due to vendor lock-in, the lack of competition and the long project cycles. Platforms are usually sold and goods, not services. After all, you don’t want the contractors to be running the ICBMs.
Digital arms are different, however, being fast and cheap to produce, and easy to replicate, and often there are questions about their legitimate civilian uses. As a result some academics are suggesting a move towards a agreements o control their use along the lines of the Wassenaar Arrangement.
[soundcloud url=”https://api.soundcloud.com/tracks/116911076″ width=”100%” height=”166″ iframe=”true” /]
My third choice for a highlight was an explanation of how you can effectively innoculate your organisation against phishing attacks, by Dan Tentler.
“How do you teach a person to duck a punch? You punch them in the face until they get it,” Tentler said.
If your people keep getting hit with viagra spam, you need to hit them with viagra spam too. Spearphish your people regularly, and if they fall for it you explain how they could have spotted the tricks. By the time they get hit with a real phishing campaign, hopefully they’ve got some “muscle memory” and won’t automatically click.
[Photo: Smart TV hack by SeungJin Lee aka @beist in progress at Breakpoint. Image by Stilgherrian. Available for re-use under a Creative Commons Attribution-NoDerivs license (CC BY-ND).]
Corrupted Nerds coverage of Breakpoint is made possible by Extra Special Supporters Adam Thomas, Justin Warren, Andrew Zammit, Cunning S7Unt, Peter Williams; Special Supporters Christopher Neal, Glen Roberts, Johan de Wit; and many others.

Headlines from Breakpoint Day 1 by Corrupted Nerds is licensed under a Creative Commons Attribution-NoDerivs 3.0 Unported License.
Based on a work at https://corruptednerds.com/blog/breakpoint-2013-day-1/.

Pingback: Stilgherrian · Weekly Wrap 177: Fire, travel, hacking and alcohol